Zero-knowledge (ZK) has emerged as a pivotal technology in the realm of blockchain scaling by powering ZK rollups.
However, what often goes under the radar is the enormous potential that ZK holds in application-layer solutions. Within these realms, ZK can safeguard data privacy and also ensure the authenticity of off-chain data.
Zk achieves these guarantees by generating proofs that can be verified easily without overwhelming hardware requirements. Although the generation of these proofs is computationally demanding, this task can be delegated to specialized hardware provers.
Research into Zk's capabilities and its subsequent integration into various applications is poised to become the next cornerstone of decentralized trust.
The Essence of Zero-Knowledge
Satoshi crafted an ingenious solution to the age-old Byzantine General’s Problem, which essentially grapples with how decentralized entities can come to a mutual agreement or truth. This breakthrough? The Proof of Work (PoW) consensus algorithm. Miners worldwide could now align their economic interests, giving birth to a global consensus system. Bitcoin also empowered users to control their private keys and verify transactions independently, ushering in a genuinely decentralized custodial ecosystem.
Ethereum brought a twist to the table through a Proof of Stake (PoS) consensus mechanism, which relies on validator incentives and penalties to maintain network security and harmony.
Decentralized ledgers enforce correctness by re-executing computations on every network node. It's like reading an entire book to verify a single word. This approach results in a computationally inefficient architecture, wherein each node must download the latest block and execute the entire set of transactions to validate conformity with the block.
Open computation isn’t just resource-intensive but also exposes a soft underbelly: a lack of privacy. This vulnerability is preyed upon by MEV exploiters, who manipulate transaction sequences for personal gain.
Recognizing these challenges, the blockchain community turned its attention towards enhancing scalability and privacy. This led to the exploration of zk-Cryptography, particularly technologies like zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) and zk-STARKs (Zero-Knowledge Scalable Transparent Argument of Knowledge). While there are nuances in how these technologies differ, let’s save that for later and look at a simplified explanation.
At its core, a ZK proof enables someone (the prover) to prove to an untrusting party (the verifier) that they possess specific knowledge without disclosing any details about that knowledge.
ZKPs possess two essential properties:
Succinct and Work-Saving: Verifying the proof is more efficient than directly checking the original data.
Privacy: Nothing about the data being proven is revealed to the verifier.
Although the technology was born in the 1990s, its initial applications were mostly confined to privacy solutions. IBM harnessed ZK in 2010 to create its identity mixer, Bluemix, while Microsoft's Election Guard leverages ZKPs to enable verifiable private elections.
ZKPs' ability to compactly validate off-chain computations has invigorated research aimed at scaling platforms like Ethereum. Over $725 million in funding flowed into ZK technology for blockchains last year, underscoring its growing significance.
While the mathematical intricacies of ZKPs are complex, developers can incorporate ZK cryptography into applications much like they do with public key cryptography. Ongoing research focuses on developing state-of-the-art provers and verifiers, with an emphasis on generating proofs efficiently and verifying them quickly.
Blockchains rely on critical off-chain data—like asset prices or information from alternate blockchains. Traditionally, oracles like Chainlink have acted as trusted data couriers, employing a network of economically incentivized validators to ensure data accuracy and integrity.
ZKPs add a new axis of trust to the cryptoeconomic landscape. With ZKPs, these applications can irrefutably demonstrate the legitimacy of off-chain data and computations, acting as vigilant 'eyes' beyond the blockchain
The ZK Landscape
Scaling
General Purpose Rollups
As Ethereum experiences rapid growth, transaction costs for ERC20 tokens and ERC721 NFTs often soar to the $5-$15 range, prompting a need to rethink scalability without compromising on decentralization.
Enter the era of rollups: Ethereum's strategic pivot towards a modular, rollup-centric framework with three distinct layers: the Data Availability (DA) layer, the Execution layer, and the Settlement layer.
There are two types of Rollups in the works: Optimistic Rollups and ZK Rollups offering Layer 2 scaling solutions that execute transactions off the Ethereum chain and settle on the Ethereum chain, inheriting its security.
Both types rely on sequencers to receive user transactions, organize them into batches, and generate proofs for commitment to the Ethereum mainnet. Optimistic Rollups rely on watchers to spot fraudulent transactions within a dispute resolution window, while ZK Rollups use Validity Proofs to ensure transaction validity without on-chain verification
Execution Layer: The execution and state storage occur off-chain in a virtual machine (VM) specific to the rollup. Every ZK rollup has a sequencer to orchestrate transactions and provers to craft proofs that validate intermediary computations. These "Validity Proofs" and minimal data are then submitted to verifier smart contracts on the Ethereum mainnet.
Most ZK Rollups are compatible with the Ethereum Virtual Machine(EVM) to support Ethereum's smart contracts. This flexibility allows developers to migrate Ethereum-based applications to Layer 2 platforms seamlessly. However, challenges persist, including prover efficiency, blockchain performance, and opcode compatibility.
Storage Layer: When it comes to storage, most rollups, including Polygon's zkEVM, Scroll, zkSync Era, and Linea, prefer to push data in a compressed format to Ethereum calldata. This approach guarantees liveness and enables users to recreate the state from Ethereum and bypass the rollup if needed.
However, some zk-rollups, such as Starknet's Validium, Matter Lab’s zkPorter, and Polygon’s Miden store their data on a different DA layer secured by a Data Availability Committee (DAC). Solutions like EigenDA and Avail exemplify this approach, aiming to boost throughput, while still benefiting from the security guarantees of the Ethereum blockchain.
Settlement Layer: ZK Rollups submit the new rollup state along with ‘Validity Proofs’ to a verifier smart contract on Ethereum. These verifiers check the Validity proofs to guarantee the correctness of state transitions in the off-chain VM and record the new state transition.
The verification process can be resource-intensive, with gas costs ranging from 300k to 5m for a single proof. Verification times can also be high, around 10 seconds. Rollups often post proofs to L1 periodically, reducing per-transaction costs by batching transactions.
ZK proofs cannot be used for consensus or transaction ordering within a rollup. Sequencers typically make consensus decisions based on their individual ruleset, with many following a first-seen principle. Efforts are ongoing to decentralize sequencers over time, with some implementing shared sequencers like Espresso.
VM based Rollups
As we discussed earlier, there are some challenges when working with L2 EVMs which can restrict computational efficiency. Ethereum's native functions, such as hash functions, often prove incompatible with ZK technology due to their resource-intensive nature. ZKSync removed support for some of these opcodes, after realizing that a majority of their costs were coming from these expensive operations.
Unlike EVMs that focus on Ethereum's instruction set, zkVM-based rollups offer the flexibility to run a wide array of software compatible with different computer architectures. These VMs, being a superset can implement different instruction sets such as RISC-V and WebAssembly, and generate ZKPs for computations.
Starknet stands as a pioneer in the realm of zkVM-based rollups. It has developed Cairo, a specialized low-level programming language that operates closer to assembly language. Polygon's Miden utilizes its own assembly language that’s closer to Move, while Delphinus and Fluent are working on WASM language-based rollups. Fluent and ZKM allow developers to build applications in general-purpose programming languages like Rust, TypeScript, C/C++, Go, and more.
zkVM-based rollups redefine Ethereum's capabilities by facilitating the construction of applications that would be difficult or impractical to develop within the confines of account-based systems.
Miden, for example, adopts a client-based proving model, where each account functions as a smart contract, and users take responsibility for creating ZKPs on their client device. These zk proofs are then submitted to the Miden rollup to update the global state. This approach allows for parallel execution of transactions and enhances privacy, as operations like token transfers and NFT swaps can occur without impacting the public state.
Rollup Frameworks
Several teams have embarked on a mission to simplify the development of Zero-Knowledge (ZK) rollups, opening the doors to a wider range of builders. These innovative frameworks provide builders with a set of comprehensive components, including sequencers, provers, Data Availability (DA) layers, and consensus layers.
Builders who leverage these frameworks gain a crucial advantage by inheriting Ethereum's robust security while retaining the freedom to make choices. They can opt to deploy a native token or utilize Ether (ETH) and have the flexibility to engage external validators or implement customized rules for their validators.
Sovereign Labs and Polygon are actively developing Software Development Kits (SDKs) that enable anyone to create ZK Layer 2 (L2) rollups with predefined rulesets and interoperable bridging for robust liquidity.
Lumoz takes a comprehensive approach, granting development teams full sovereignty over their rollups through dedicated Proof of Work (PoW) consensus, dedicated proving networks, and communication channels with other rollups.
LayerN facilitates a hybrid zk-OP (Zero-Knowledge-Operator) architecture and boasts the promise of transaction fees that are a thousand times cheaper than Ethereum.
Eclipse recently made a significant announcement by unveiling a general-purpose L2 which serves as an example that combines different modular elements - Solana’s execution machine that posts DA to Celestia and generates ZK proofs using Risc0 to settle on Ethereum. These experiments are driving forward the modular thesis and aim to combine Solana's high-performance Ethereum Virtual Machine (EVM) with the security of Ethereum.
Rollups-as-a-Service
Rollups-as-a-Service (RaaS) simplifies the landscape of Rollup frameworks and Software Development Kits (SDKs), offering a layer of abstraction that facilitates the effortless deployment, maintenance, and creation of custom, production-grade application-specific rollups.
RaaS liberates developers from the complexities of infrastructure management and monitoring network performance, enabling them to concentrate on building the application layer. What used to demand extensive engineering hours now translates into a straightforward 10-minute, no-code deployment process.
Think of them as the AWS (Amazon Web Services) of Rollups, simplifying the rollup deployment and development process.
With platforms such as Vistara and Gateway, users gain the power to mix and match modular components, swiftly spinning up personalized rollups tailored to their needs in mere seconds.
This modular approach empowers developers to craft ZK rollups that align precisely with their unique objectives. From Execution Virtual Machines (VMs) and Data Availability (DA) layers to Sequencers, Bridges, and Provers, developers have the flexibility to select components that suit their requirements.
Special Purpose Rollups
Despite the advancements in general-purpose rollups, there are limits to scaling due to competition for L2 block space and rising L1 batch posting costs. Specific dApps require tailored functionality, such as fast finality for DeFi, low latency for gaming, and privacy for enterprise blockchains, necessitating application-specific rollups.
Leading the way is Starknet's ecosystem which processed more than 418M transactions, with applications like dYdX, Sorare, and Immutable utilizing app-specific rollups built on Starkware's Starkex technology. Starknet’s operator aggregates transactions, batches them, and provides ZK proofs to the Ethereum main chain, ensuring security and privacy at reduced costs.
Loopring, a ZK rollup, focuses exclusively on DeFi use cases, offering features like Block Trade for instant execution with CEX-level liquidity. Myria, another ZK rollup, caters to gaming applications, emphasizing low transaction costs. Canto, announced recently that it is migrating to an L2 focused on Real World Assets utilizing Polygon’s Chain Development Kit.
Privacy
As Web3 technologies scale rapidly, attracting millions of users, the pressing issue of privacy still lurks—particularly for institutions, banks, and businesses, which often find themselves obligated by legal requirements to safeguard their financial transactions.
ZK proofs add an element of protection from prying eyes, and this was the initial use case popularized by zCash. Zcash uses zk-SNARKs to prove that a transaction is valid without revealing any information about the sender, receiver, or transaction amount. Wallet balances are not stored as plaintext but stored as ‘Commitment Notes’
This cryptographic technique allows users to conceal the details of their transactions while still proving that they possess sufficient funds and follow the protocol's rules:
Value Conservation: It confirms that the total amount of coins entering the transaction (input) is equal to the total amount of coins leaving the transaction (output), without revealing the actual amounts.
Spending Authority: It proves that the sender has the correct private spending keys for the input they are using, thus confirming their authority to spend the coins.
Double-Spending Prevention: It certifies that the coins haven't been spent before, preventing double-spending.
Privacy focused L1s
A host of protocols like Aleo, Aleph Zero, Ironfish, and Mina are pushing the boundaries even further, specializing in Layer 1 solutions that prioritize privacy. Unlike Ethereum's account-based framework, which is not optimum for privacy, these protocols adopt a modified version of Bitcoin's UTXO model.
Consensus Models: Each of these privacy-centric protocols employs distinct consensus models. For example, Aleo utilizes a Sustainable Proof of Work (SPoW) mechanism, where the "work" involves generating zk proofs rather than resource-intensive mining. Ironfish follows a Proof of Work (PoW) model akin to Bitcoin, generating coins solely through mining without an Initial Coin Offering (ICO). Aztec, originally designed as a Layer 1 (L1) solution, has transitioned to a Layer 2 (L2) framework, settling on the Ethereum network.
Redefining Networking Layers: Beyond consensus, these protocols reimagine networking layers, championing peer-to-peer data exchanges to maximize privacy. For instance, Ironfish uses a combination of WebRTC and WebSockets to establish connections with nodes. Users can establish direct connections, conduct transactions, create ZKPs to validate adherence to rules, and then settle transactions on the blockchain—all while preserving their privacy.
Privacy focused L2s
Meanwhile, projects such as Aztec and Ola are dedicated to enhancing privacy on the Ethereum network by enabling ZK rollups with private accounts and encrypted transactions. Both projects are developing their own zkVMs, placing a high emphasis on managing private accounts, rather than solely focusing on Ethereum compatibility.
ZK Apps
Applications leverage the privacy capabilities of ZKPs to bring trust to off-chain data and computations. We can condense most of the use cases into the following categories:
a. Secure Sharing of Secrets: ZK technologies empower users to confidentially share secrets through a trustless settlement layer. Prominent applications such as zkMail and zkVoting protocols facilitate end-to-end encrypted data sharing, ensuring robust privacy.
b. Confidential On-Chain Identities: ZK Apps enable users to create discreet on-chain identities in a composable manner, transcending the limitations of conventional data obfuscation methods like mixing.
c. Offchain Security Assurances: Leveraging ZK technology provides robust off-chain security assurances, ensuring the integrity and intended state of extensive off-chain data and computations.
d. Interoperable Trust: ZK-powered oracles and bridges assume a pivotal role in upholding cryptographic integrity when bridging off-chain data onto blockchain networks.
Privacy Middleware
Rather than creating entirely new blockchains that come with native privacy, privacy middleware protocols introduce privacy mechanisms into existing blockchain networks. These platforms introduce a privacy layer that acts as an intermediary between user addresses and anonymous or "stealth" addresses, offering a practical approach to privacy enhancement.
Tornado Cash, inspired by Zcash's privacy model, deployed an Ethereum-based smart contract to manage user balances stored in stealth addresses. Using zero-knowledge proofs, the protocol verifies each transaction's integrity, ensuring that users cannot withdraw funds exceeding their account balance after they mixed funds. However, Tornado Cash encountered regulatory challenges, as malevolent actors exploited its privacy features for illicit purposes.
Recognizing the need for compliance, industry leaders like Vitalik Buterin and Ameen Soleimani are pioneering next-generation privacy pool models that balance robust privacy with adherence to regulations. These models explore various methodologies:
Blacklist Screening: Ability to prohibit deposits from addresses listed on FATF's blacklist, ensuring the protocol's legitimate use for privacy-enhancing activities.
User-Controlled Viewing Keys: Users maintain read-only keys that can be selectively shared with regulatory agencies. These keys verify the source of funds and tax obligations while confirming that funds do not originate from blacklisted addresses.
Server-Controlled Viewing Keys: In this setup, the protocol retains the ability to view all user funds and transactions, providing selective disclosure to regulatory bodies for enhanced compliance.
Platforms like Panther and Railgun offer shielded tokens that are minted by depositing funds into these platforms to get shielded assets which can be used across blockchains like Ethereum, BSC, Polygon, Solana, and more.
Nocturne leverages Multi-Party Computation (MPC) and Account Aggregators (AA) to create a stealth address layer. Instead of minting zk assets, these addresses are designed for interaction with protocols. Users deposit funds into a Deposit Manager, which mixes all user funds and provides stealth addresses for each application interaction. DApps never access the source of these addresses, enhancing privacy.
DEX
In response to the growing demand for secure and private asset exchanges within the institutional space, development teams are actively exploring the realm of ZK-based Decentralized Exchanges (DEXes). Unlike Automated Market Makers (AMMs), ZK-based DEXes utilize order books, offering a slew of benefits including enhanced liquidity, gas-free transactions, unlimited trading pairs, diverse order types, and a user-friendly interface.
Let’s dig into Brine as an example. Brine employs a hybrid model that effectively splits its operations between off-chain and on-chain components:
Off-Chain Section: In the off-chain section, Brine manages wallet data and real-time status of all orders and trades. This off-chain component plays a crucial role in the efficient execution of orders and maintaining an up-to-date order book.
On-Chain Section: The on-chain segment handles state commitments and system assets. To ensure the security and integrity of transactions, Brine utilizes the STARK prover, and these proofs are subsequently validated on the Ethereum network through a dedicated StarkEx contract, guaranteeing the accuracy of the state transitions.
Because Brine's orders are stored off-chain, the platform can accommodate a variety of order types, including limit and stop orders. Market makers can step in to provide liquidity, earning fees similar to those seen on centralized exchanges (CEXs).
Brine's matching engine boasts impressive scalability, with the capability to handle up to 600,000 TPS. This outperforms the limitations typically associated with AMMs. Importantly, since only the cryptographic proofs are posted on-chain, traders enjoy 100% privacy regarding their positions.
In addition to Brine, platforms like Zkex and Satori are also making waves in the market by enabling the trading of derivatives and perpetual contracts using a similar mechanism.
Interoperability
Bridging data and assets between two chains has often relied on trusted groups of validators or trusted multi-signature custodians to ensure the accurate transmission of data. This reliance on external validation has resulted in significant security vulnerabilities, as evidenced by breaches in bridges like Nomad, Wormhole, and Ronin, cumulatively amounting to over $1.5 billion in losses. These traditional bridges often hinge on an external committee to lock assets on the originating chain before minting corresponding assets on the target chain.
The introduction of Zero-Knowledge (ZK) based light clients offers a revolutionary advancement. These light clients use ZK proofs to validate consensus changes on the source chain. Running light clients of entire blockchains would be computationally expensive so ZK bridges send zkSNARK proofs of consensus changes to the execution layer of the destination chain. The destination chain validates the correctness of consensus changes by verifying the ZK proof. This approach significantly reduces the computational cost of running a node, facilitating interoperability without relying on trust assumptions.
Succinct, for instance, is developing a light client named Telepathy that can validate Ethereum's consensus for just 300,000 gas on EVM chains. These light clients can support various functions on the destination chain, including:
Sending arbitrary messages across chains to govern cross-chain deployments.
Reading Ethereum validator stake and balances for Layer 2 solutions and re-staking protocols.
Facilitating liquidity bridges between chains without relying on lock/mint protocols.
Accessing Chainlink oracle data from Ethereum across destination chains for Layer 2 Automated Market Makers (AMMs) and DeFi protocols.
Polyhedra and zkLink are focusing on bridging liquidity across multiple chains. Rather than maintaining its own liquidity pools on each connected network, zklink aims to aggregate liquidity and merge tokens across all dApps utilizing zkLink infrastructure.
Oracles and Coprocessors
Oracles can be divided into two main types
Input Oracles- Bring off-chain data to on-chain context (ex: Chainlink Price Feeds)
Output Oracles- Deliver on-chain data to off-chain context for advanced computation (The Graph)
Smart contracts have inherent limitations, especially when it comes to handling complex computations such as floating-point operations, intensive calculations, or statistical analyses. This is where Output Oracles come to the forefront, addressing these computational challenges by offloading them to external systems.
Staking-based oracles such as Chainlink and the Graph run a group of validators who are rewarded for importing data from the real world(such as prices on CEXs or weather data) and performing calculations on this data. However, a security concern arises when the total amount staked is lower than the potential value that could be stolen. Hackers can exploit this imbalance to manipulate oracle data, leading to frequent attacks and exploitation of arbitrage opportunities.
This is where ZK Oracles step in, specifically in the domain of Output oracles. They ensure the accuracy of computations executed off-chain by supplying zk proofs to verify that the computations occurred as intended. This has given rise to a new category called co-processors.
HyperOracle is pioneering ‘trustless’ oracles by utilizing specialized oracle nodes that generate Zero-Knowledge (zk) proofs along with the transmitted data to verifier contracts on the Ethereum blockchain.
This approach shifts the security model to a "1 of N" model, where even if one node submits correct data, verifier contracts can detect any discrepancies. This setup guarantees 100% computational integrity for off-chain computations while reducing finality to just 12 seconds, aligning with Ethereum's block time.
Addressing another challenge, Axiom provides a trustless mechanism for accessing historical state data on Ethereum. Due to the state-machine nature of Ethereum, smart contracts can only access the current state and rely on centralized off-chain oracles to access historical state data.
Axiom resolves this issue by supplying Zero-Knowledge proofs to validate the authenticity of block headers, states, transactions, and receipts from any past Ethereum block.
Herodotus specializes in storage proofs, which are essentially ZK proofs confirming the inclusion of data in the state root across L1s and L2s. Developers can build cross-chain apps such as lending apps that secure loans on one chain by providing collateral on another chain, and gaming apps that can utilize NFT assets on another chain.
Identity / Proof of Personhood
The privacy guarantees of ZKPs have created an opportunity to design new cryptographic primitives across every aspect of identity: proof of location, proof of ownership, proof of voice, education, experience, healthcare data, and KYC.
Sismo is a great example of ZKPs in this segment. The team is working on developing ZK badges that enable users to selectively share their personal data with web3 apps and users. A ZK badge is a soul-bound token that categorizes users into specific groups based on their personal data. For instance, a user can prove that they are a long-term Ethereum user, a contributor to a particular GitHub repository, or an American citizen by generating a ZK proof that validates the conditions. After validating the proof, Sismo grants the user the badge that corresponds to their personal data. The badge marks the user’s identity without actually revealing any sensitive details.
Worldcoin represents another innovative application of ZKPs, establishing the World ID as an open and permissionless identity protocol. The protocol utilizes iris biometrics for precise identity verification, converting a high-resolution iris scan into a compressed form through a convolutional neural network. This data is inserted into their Semaphore ZKP implementation to generate an identity commitment which is stored in the World ID contract.
To prove their identity, a user provides his World ID, which is examined against the entire list to verify membership, granting access to useful functions, such as voting and one-time airdrops.

Verifiable computation
Proof of computation is a cryptographic technique that allows one party to prove to another that a particular calculation has been carried out correctly, without disclosing any sensitive information about the input, output, or computation itself.
Risczero’s virtual machine generates ZKP computational receipts when a piece of code runs on their machine -this "execution trace" enables anyone to verify the record of the state of the machine at each clock cycle of the computation while maintaining data privacy. It's like having a digital notary for computations on the RISC-V architecture.
This opens up a world of possibilities such as:
Verify a computation has happened without full disclosure - ZK Proof of Exploit, which allows white hat hackers to report real-time vulnerabilities in smart contracts without disclosing confidential details of the exploit. Additionally, ZK Proof of Storage, used by Filecoin ensures that miners store a copy of the data at any given time.
Verify the authenticity of media- Distinguishing genuine images from manipulated ones has become an escalating challenge, fueling the proliferation of fake news. The Coalition for Content Provenance and Authenticity (C2PA) proposed a standard to verify image provenance to ensure that the images are indeed authentic and captured in the purported context. The standard requires cameras to “digitally sign” each photo taken along with a series of assertions about the photo (e.g., location, timestamp). However, before the images are posted on the internet, they may undergo resizing, cropping, and enhancement which might alter these assertions. Boneh and his team have implemented ZKPs for various photo edits, including cropping, transposing, flipping, rotating, and adjusting contrast/brightness. As a result, any user can easily check the proof to verify if a news story is authentic without relying on ‘community notes’.
Verification of financial information- By utilizing ZK attestation, individuals can transform their KYC data into a ZK proof on their client device and share it with the Dapp for compliance without revealing sensitive information. Alternatively, banks can sign ZK proofs to affirm the integrity of credit scores. While Fintech apps rely on Plaid to verify such data, permission is required from banks to set up such integrations.
Protocols like Reclaim, zkPass, and Chainlink’s DECO bypass these permission requirements and store financial data as composable zk proofs, usable by any Dapp. These protocols work by functioning as a proxy between the website server and the client device, generating a TLS receipt to ensure the accuracy of the data. They allow the trustless import of various data, such as Github repos, Facebook posts, Bank Balances, Land records, Tax documents, and Gaming achievements, all recorded as zk proofs on-chain. These protocols liberate web2 data from centralized, permissioned servers and transform them into composable web3 credentials.Verify the authenticity of large models - Giza, Space and Time, and Modulus Labs are working on verifiable algorithmic integrity - concentrating on ZKML.
Algorithms have an immense influence on our daily lives, powering everything from online searches and social media to personalized recommendations, controlling our attention, and shaping our beliefs. Given their vast importance, the transparency and openness of these algorithms are of critical importance, as users deserve to know how these algorithms work and how they're being used.
ZKML technology allows users to verify if platforms like Twitter are genuinely using the algorithms they claim to, by providing cryptographic proofs for the final output scores of individual posts. ZKPs offer a promising avenue for holding tech companies accountable, and their application extends beyond social media to various sectors, including AI and healthcare.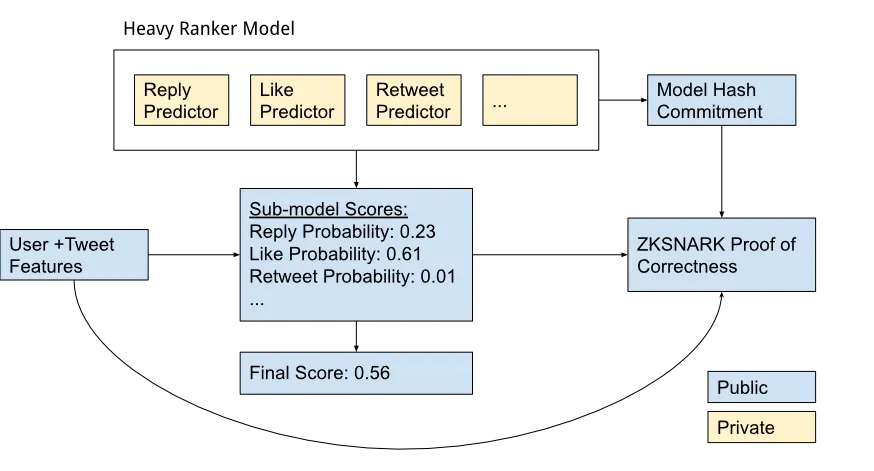
Daniel Kang demonstrates how Twitter can publish a score with every tweet to verify that the rank is accurate
Private Computation
(ZKPs) are powerful on their own, but when combined with other cryptographic technologies like Multi-Party Computation (MPC), Fully Homomorphic Encryption (FHE), and Trusted Execution Environments (TEEs), they open up new realms of secure and private designs.
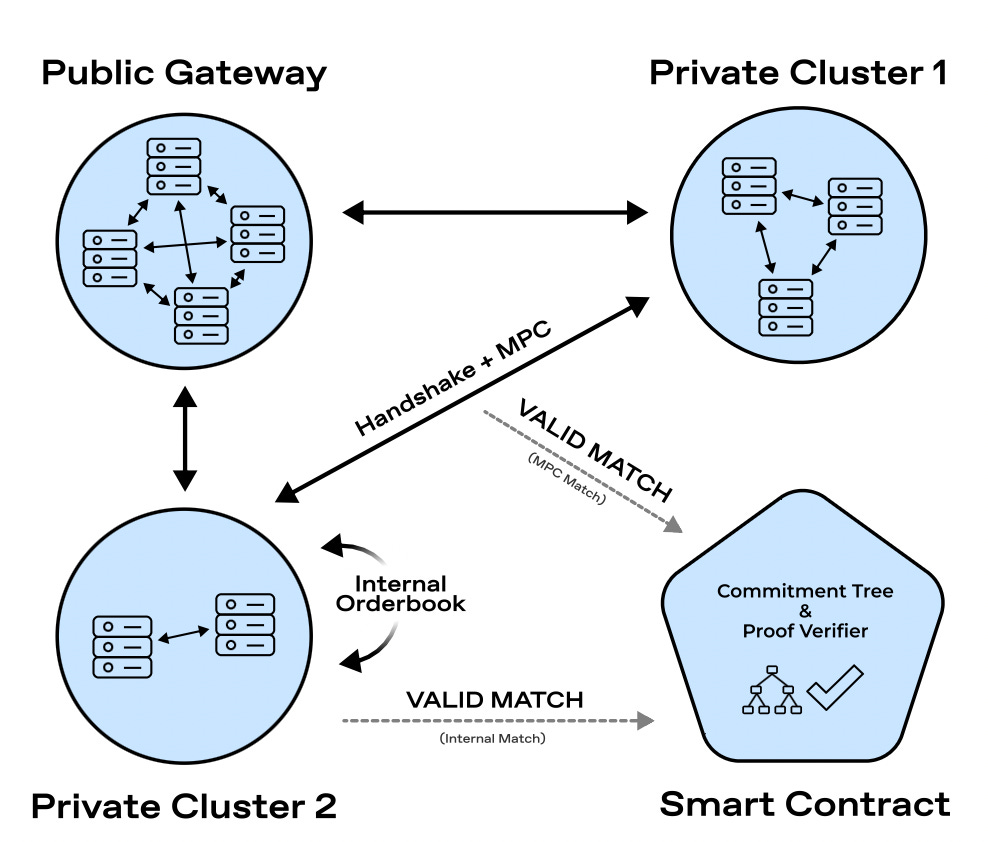
Renegade is working on an on-chain dark pool, ensuring traders enjoy complete privacy both before and after executing trades. In traditional setups, when two parties wish to exchange information and assets, they must rely on a central server to decrypt and process the data. However, if either party gains insight into the output and aborts the connection before the token swap, it could result in information leakage and market manipulation.
To address this, Renegade introduces a peer-to-peer gossip network with multiple relayers. When a trader seeks to trade, relayers identify counterparties and establish an MPC connection, safeguarding trade information from third-party exposure.
MPC, a cryptographic technique, enables multiple parties to collaboratively compute a function output without revealing their inputs. Traders can exchange assets without revealing their entire balances and this core functionality forms the basis of a full dark pool, eliminating the need for a trusted operator. However, MPC protocols themselves have no guarantees about the validity of input data. Renegade generates a zk-SNARK proof inside the MPC computation, ensuring that traders' balances align with their claims.
Fully Homomorphic Encryption empowers cloud computations on encrypted data, protecting sensitive information from third-party access. Meanwhile, ZKPs provide a means to prove the correctness of computations through succinct verifiable proofs.
The convergence of MPC, FHE, and ZKPs opens the door to new applications. zkHoldem revolutionizes on-chain poker by generating ZK proofs for every shuffle and deal, ensuring provably fair gaming. By also implementing MPC technology to hide players' cards even from their servers, zkHoldem raises the bar for on-chain gaming integrity.
ZK Tooling
Proving systems
A proof system is a two-party protocol involving a set of rules and procedures that enable the prover to convince the verifier of the truthfulness of a statement. Multiple ZKP systems are at developers' disposal, each with its unique strengths and challenges:
zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge):
Pros: Compact proof size; rapid verification.
Cons: Requires a "trusted setup" – a one-time initialization that, if mishandled, can enable fake proofs.
zk-STARKs (Zero-Knowledge Scalable Transparent Arguments of Knowledge):
Pros: No trusted setup needed; safeguarded against quantum threats.
Cons: Larger proof size; elevated computational demands.
Bulletproofs:
Pros: Avoids the need for a trusted setup; reasonably small proof size.
Cons: Verification and creation are more time-consuming than zk-SNARKs.
PLONK:
Pros: Boasts efficient arithmetic and a streamlined setup.
Cons: Still a topic of ongoing research; not as established.
Software
Domain Specific Languages transform abstract logic into circuit representations that can be consumed by proving systems. DSLs express higher-level logic in a form that is very close to assembly language. Some like Aztec’s Noir are compatible with multiple proving systems making them a great choice for developers. Yet, the complexity of these languages acts as a barrier, making circuit design a challenge for most developers.
A wave of innovation is sweeping across the ZKP landscape, with many teams crafting higher-level languages that abstract away the complexities of assembly languages.
Two examples of these are SnarkyJS, a TypeScript framework tailored for the Mina blockchain, and Polylang, another TypeScript framework developed by Polybase Labs that collaborates with Miden's VM.
Broadly, ZK tools target three core objectives: versatility, user-friendliness, and performance. Solidity is not friendly for generating ZK representations, so the Starknet team created Cairo, which is tailor-made for creating STARK-based smart contracts.
Ethereum's aspirations include the integration of ZK-EVM into its core protocol through a type 0 zkEVM. However, this ambition comes with its set of challenges as Ethereum wasn’t designed for zk friendliness, and generating proofs for Ethereum blocks is computationally expensive. RiscZero recently announced their project Zeth which can prove all aspects of Ethereum, from every EVM opcode and EIP to the block construction but it’s still a long way before ZK can be enshrined into Ethereum.
Hardware
The rise of the gaming industry has spurred significant advancements in both software and hardware development, transforming PCs and gaming consoles. In 1993, Nvidia entered the scene with a focus on GPUs tailored for 3D acceleration, catering to the burgeoning gaming market. As the AI and machine learning (ML) craze gained momentum, Nvidia recognized the untapped potential of its GPUs for accelerating complex computations in these fields. Consequently, they pivoted towards repurposing GPUs to enhance the efficiency of AI and ML tasks, ultimately securing a dominant 95% share of the AI chip market.
In a similar vein, we anticipate that Zero-Knowledge (ZK) technology will usher in a new era of specialized silicon hardware. This hardware - GPUs, FPGAs, and ASICs will be designed to accelerate the generation and validation of proofs while maintaining cost-effectiveness.
Generation ZK proofs on user hardware is really slow but necessary to maintain privacy. Hashing 10kb of data with SHA2 on a mobile takes a few milliseconds, but generating a ZK proof of this would take at least 2 minutes.
Hardware acceleration teams like Ingoyama and Cysic can generate proofs on the cloud through specialized hardware and return proofs to users.
Protocols that require heavy zk computation can also collaborate with specialized hardware providers, ensuring optimal performance and competitive rates. For example, Ulvetenna operates FPGA clusters that are purpose-built for ZKP rollup computation.
These startups offer a spectrum of options, from online Software as a Service (SaaS) models to the sale of dedicated hardware to organizations. Some offer consulting services for designing custom circuits tailored to the specific needs of applications as well.
Proof markets
For emerging developers requiring ZK proving, establishing contracts with specialized hardware providers and navigating the landscape for cost-efficient solutions can pose significant challenges.
Proof markets such as RiscZero’s Bonsai, Nil’s Proof Market, and Marlin’s Kalypso serve as bridges, connecting startups in need of ZKP generators with those offering proof generation services. Within these marketplaces, there is a strong emphasis on two critical aspects of proof generation: the associated costs and the time required for producing proofs.
Broady, there are two user segments - privacy-conscious consumers and efficiency-driven startups
Client-side proving: Individuals want to generate ZKPs to preserve privacy, aiming to keep their sensitive information shielded from centralized entities. Their best bet is to generate the ZKPs on mobile devices or laptops but since this is time-consuming, they are looking to offload this to dedicated accelerators. Researchers are actively exploring private delegation methods using protocols like DIZK, which aim to ensure that no single worker gains access to the complete secret, maximizing privacy and security.
Server-side proving: Startups need massive proving capabilities, such as a decentralized exchange (DEX) that generates proofs for all the transactions flowing through its system and requires swift processing capabilities to eliminate latency in their application's performance.
Beyond Trust
At Polygon Ventures, we've had the privilege of closely observing the evolution of ZK technology. This journey has allowed us to collaborate with pioneers like Jordi and Daniel, delving into the inner workings of this transformative technology.
In the cyclical dance of bear and bull markets, infrastructure often emerges as the unsung hero during downturns, fortifying itself for the ensuing upturn. Reflecting upon the previous bull market, ZK technology was merely in its embryonic stage. Fast forward to today, and it is truly inspiring to see the exponential growth in ZK applications, the monumental advancements in ZK scaling, and the development of a trustless computational paradigm that has expanded significantly.
ZK technology has been advancing at an incredible pace; applications which seemed impractical a few years ago are now a reality. New ZK projects can choose from a variety of libraries, DSLs, zkVMs and other tools. - Daniel Lubarov, PLONKY2
We're transitioning to an era where centralized institutions, once deemed infallible, are being viewed with increasing skepticism. While centralized stalwarts like Google, Twitter, and Meta wield the power to curate and censor, it's evident that the winds of change are brewing.
As with any promising technology, ZK is not without its challenges. The journey to secure ZKPs will take time, reminiscent of Ethereum's early days of smart contract vulnerabilities. Despite these hurdles, ZK holds within it a promise — a promise to fundamentally transform the way we interact and trust each other.
If you are building something innovative in this domain, we'd love to join forces and unlock the vast possibilities of this space.
Big thanks to Nathan and Daniel for their feedback. Disclosure - We have invested in many of the projects listed here including Space and Time, Airchains, Ingoyama, ZKLink, Eclipse, and Gateway.